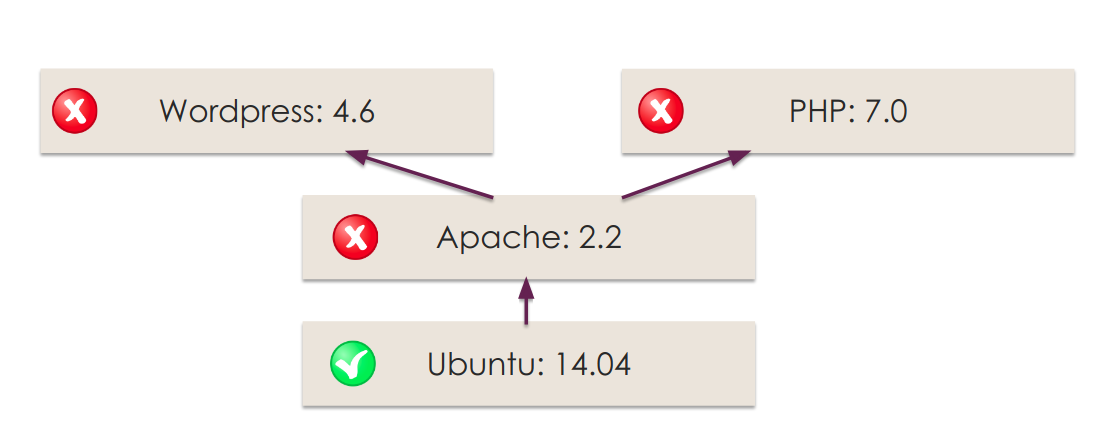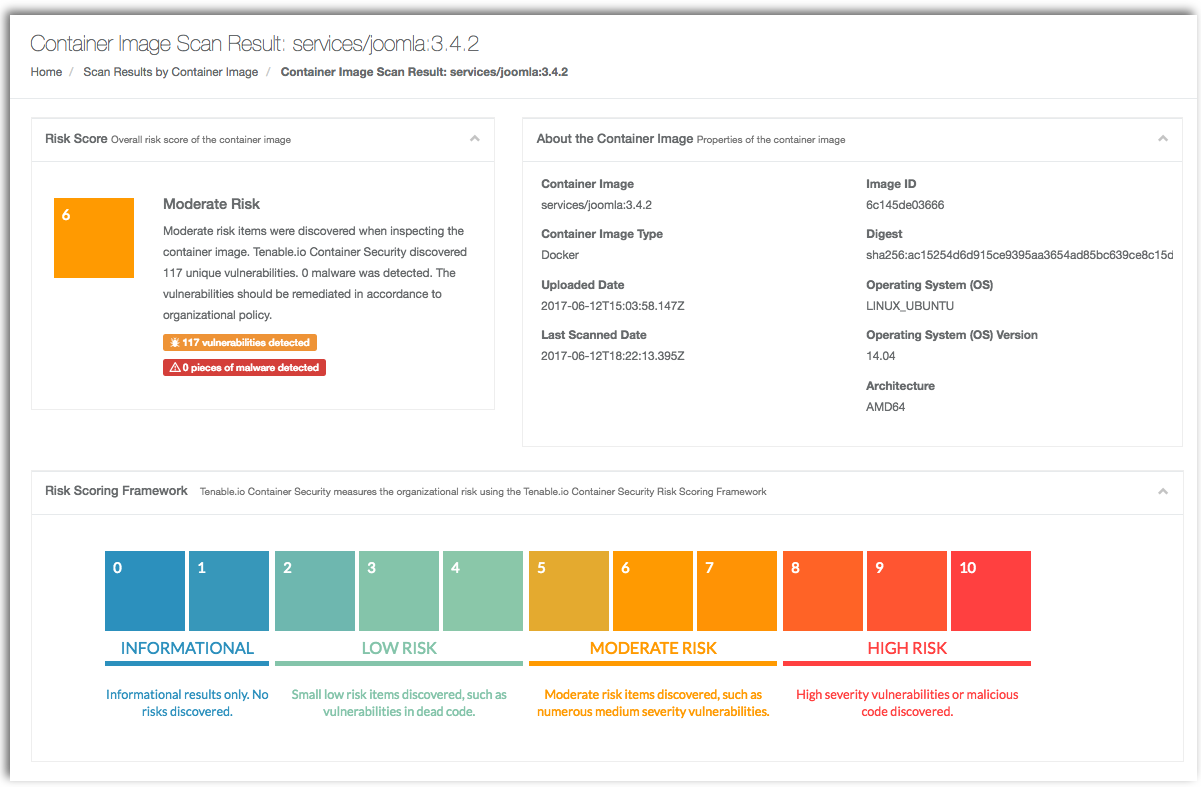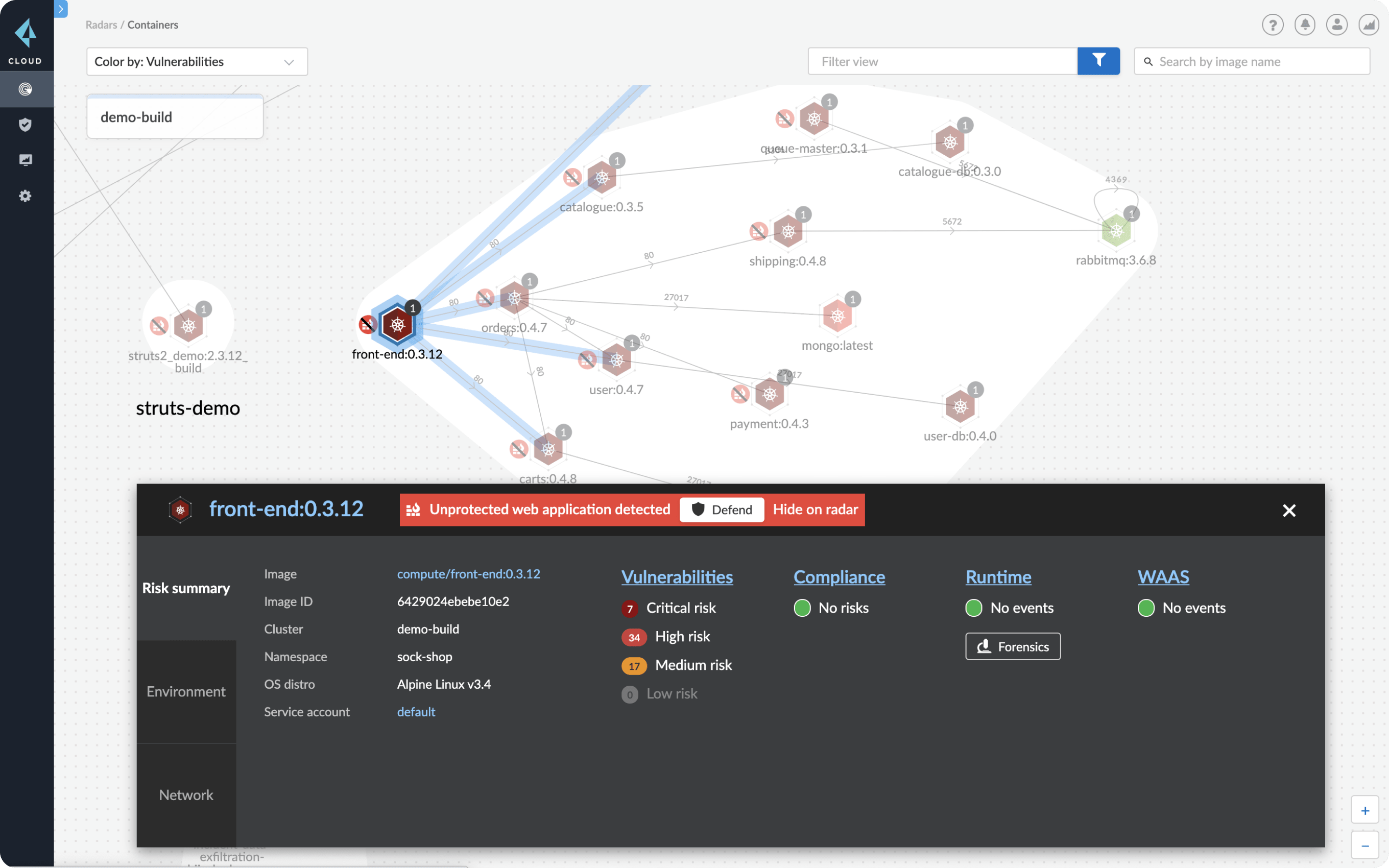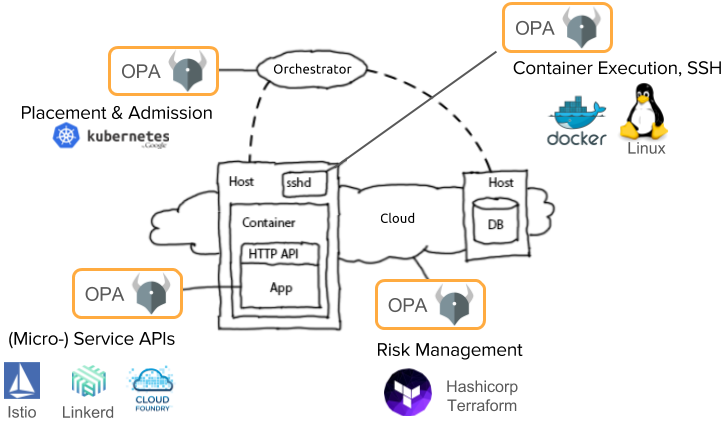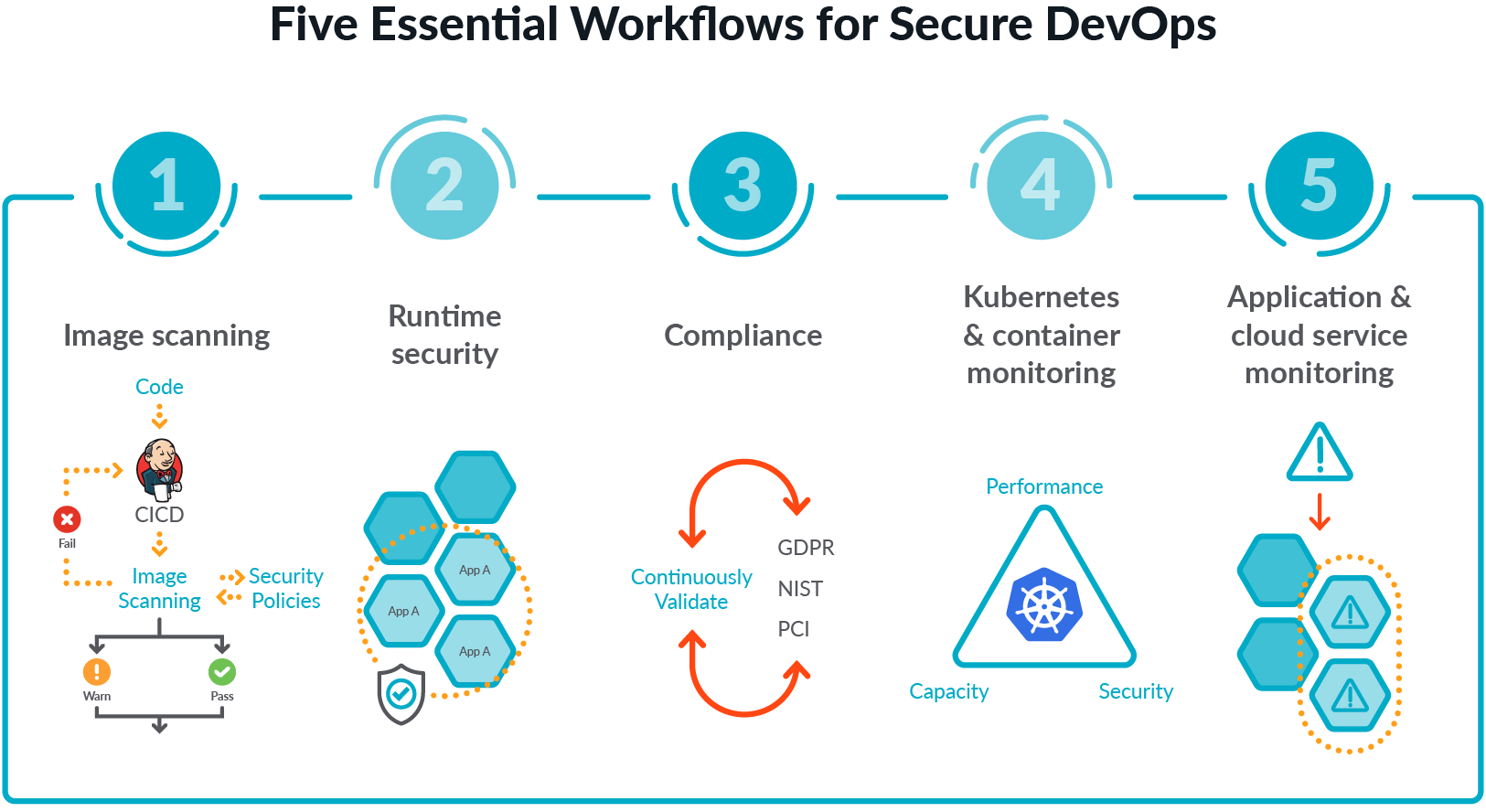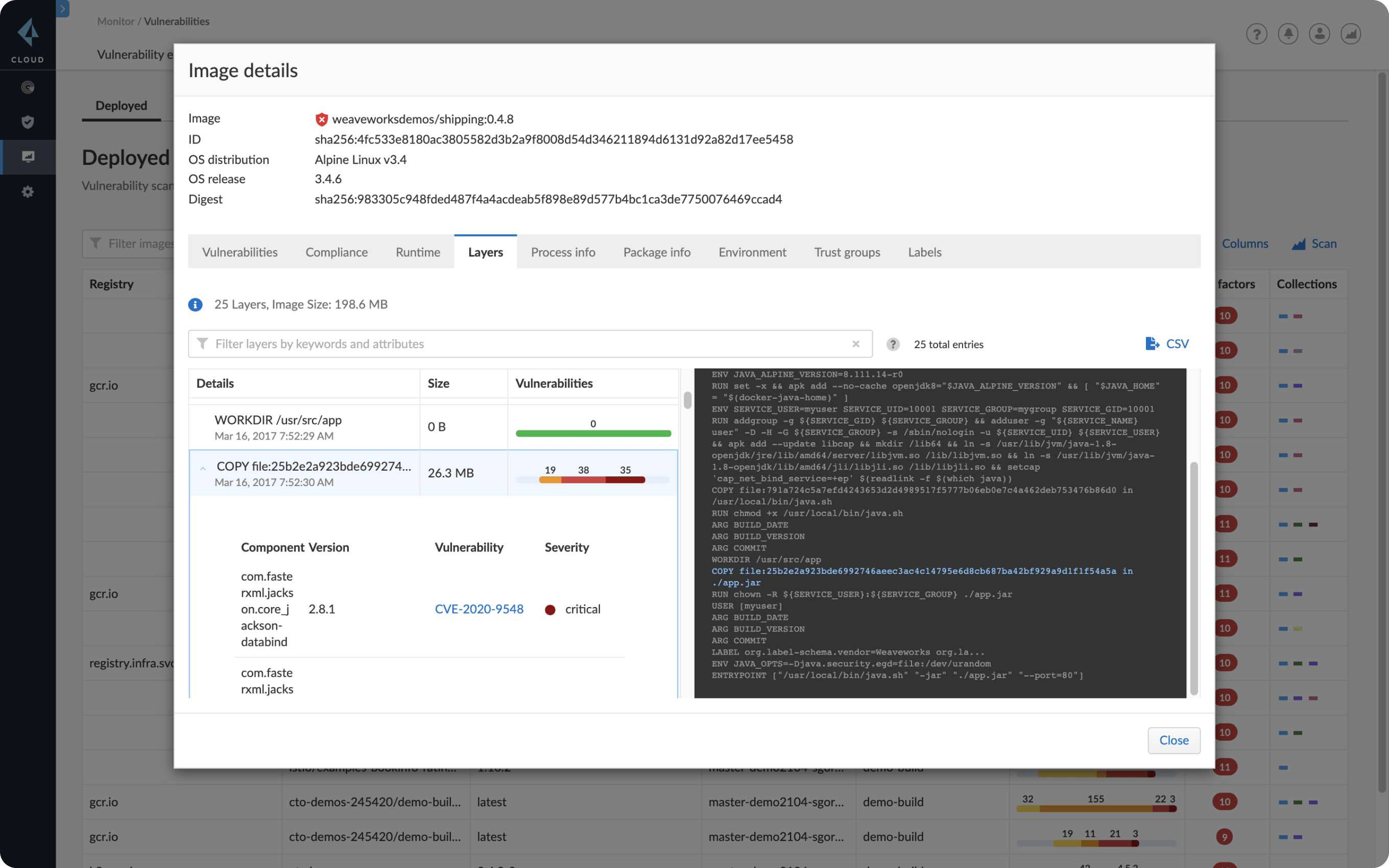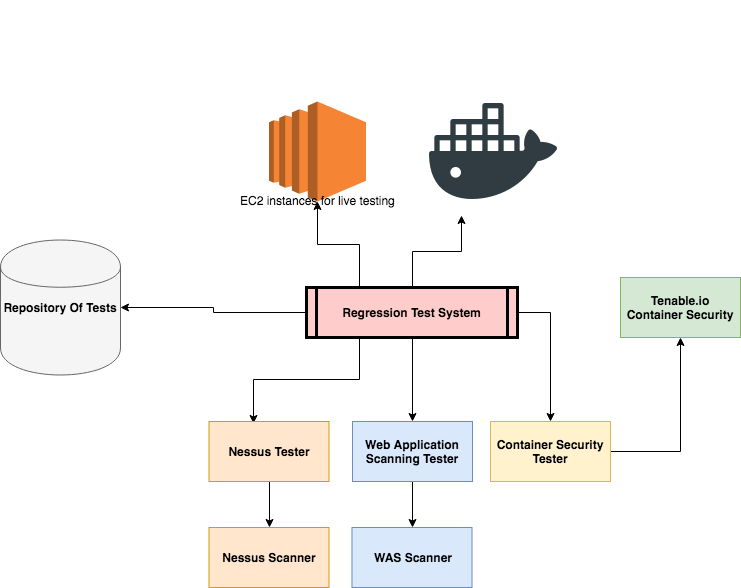
Automated Reconciliation of Vulnerability Detection Across Scan Engines | by Sasan Padidar | Tenable TechBlog | Medium

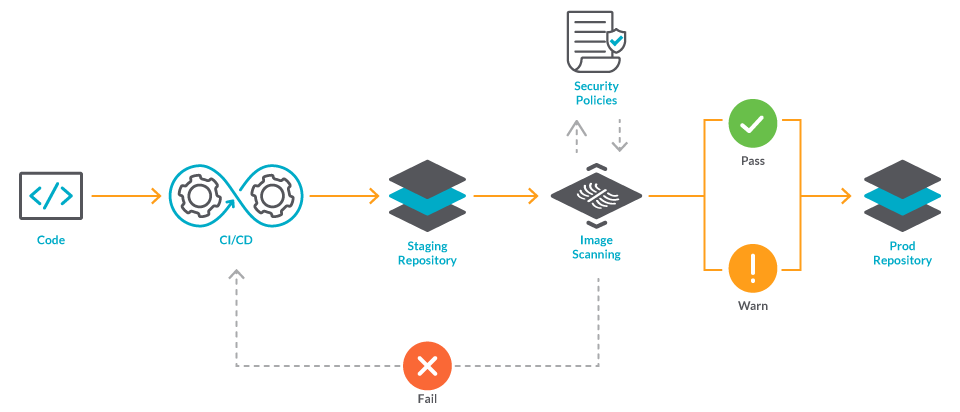
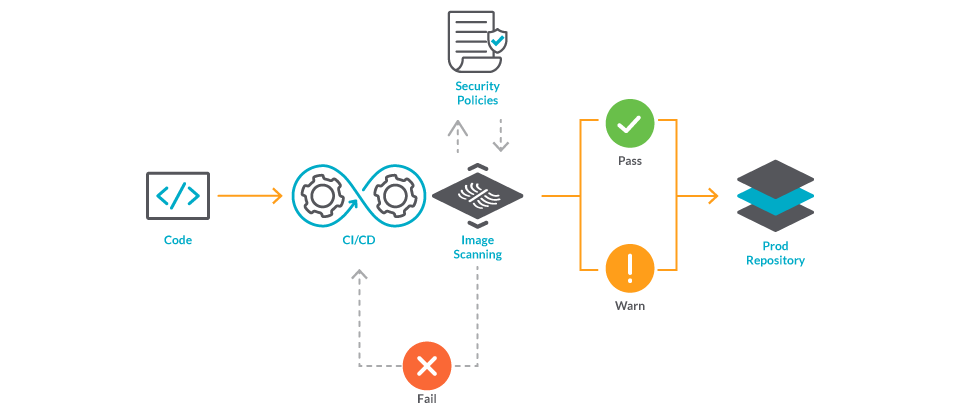
Adding Image Security Scanning to a CI/CD pipeline | by Larbi Youcef Mohamed Reda | alter way | Medium

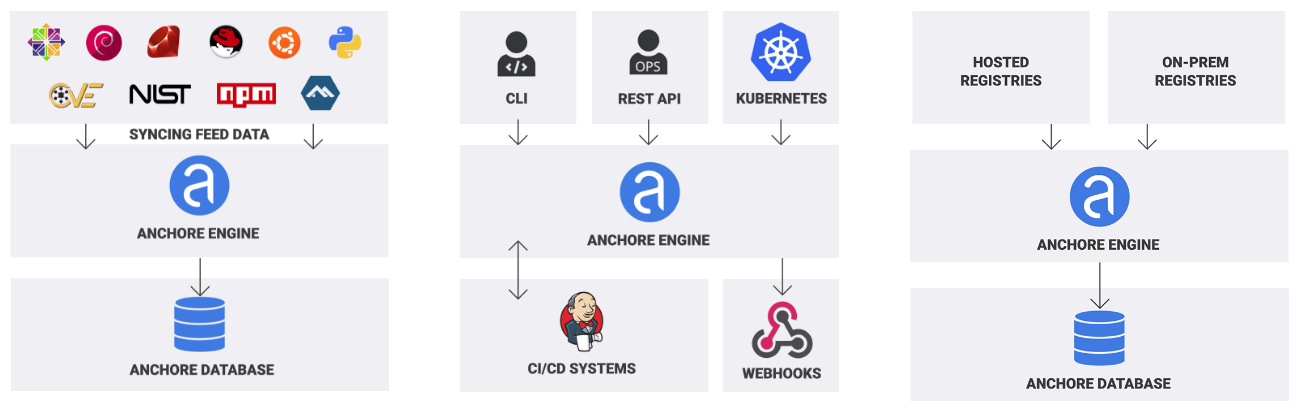
Step by step guide to integrate opensource container security scanner (Anchore engine) with CICD tool (Jenkins). | by Tanvir Ahmed | FAUN Publication

Operator best practices - Container image management in Azure Kubernetes Services (AKS) - Azure Kubernetes Service | Microsoft Docs

Step by step guide to integrate opensource container security scanner (Anchore engine) with CICD tool (Jenkins). | by Tanvir Ahmed | FAUN Publication